Remote access software, also called remote desktop software, is a popular type of application that allows a user to remotely access another computer, whether to view the interface or to actually take control of its operations. “Remote” can refer to a connection over an in-house network or halfway across the world. In today’s modern workplace, where more and more people work remotely or travel routinely for their job, even basic remote access capabilities can transform what is possible for a business.

Many people may think of remote access software as a means of facilitating employee productivity and peer-to-peer collaboration—think sharing slideshows with a remote office or quickly moving a file from a home computer to a work device just before a big meeting. However, potentially the greater value of remote access tools pertains to IT troubleshooting, where the ability to view and control end-user computers can streamline workflows, expand the scope of operations, and ultimately improve how technicians perform their jobs.
What Is Remote Access Software?
In short, remote access software allows a user to access a computer from a remote location. The user on the local workstation or device, known as the “client,” can use their screen to display the screen of another PC, known as the “server.” In some cases, remote access is used for long-distance collaboration, but when used specifically for remote management or administration, the client typically accesses the server in order to troubleshoot a specific issue. This is often faster than an in-person visit—and equally effective.
By using remote desktop software, an IT professional is able to control the mouse and keyboard actions of the server from their own local device. In other words, they are able to see and manipulate the display of the remote device, essentially in real time. This graphical screen-sharing is known as virtual network computing (VNC) and utilizes the Remote Framebuffer Protocol (RFB). VNC is integral to remote tools, and other variations of VNC offer additional functions like file sharing.
Some remote access solutions use a Remote Desktop Protocol (RDP) (a proprietary Microsoft protocol) to achieve a remote connection. Versions of this also exist for macOS, Linux, and other operating systems. RDP enables the server to listen on TCP port 3389 and UDP port 3389 and allow a connection if a request is made. Besides RDP, some software products may even have their own proprietary remote-control protocols.
Connections to remote devices don’t always have to occur within a corporate network or firewall, and IT professionals sometimes use internet proxy servers to achieve connectivity. That said, remote access is typically set up over a LAN, WAN, or VPN. It can be inherently risky to share device access, so it’s important to use a vetted program and follow security best practices no matter how a connection is made.
Remote Access Software Features
There are a variety of free, built-in, and commercial remote access products available, but these solutions are not all equipped with equal capabilities. When choosing a software solution, it’s important to consider which potential features are most essential for your unique needs. Different remote access tools offer different sets of features, and the protocols behind these features may offer varying degrees of security and functionality.
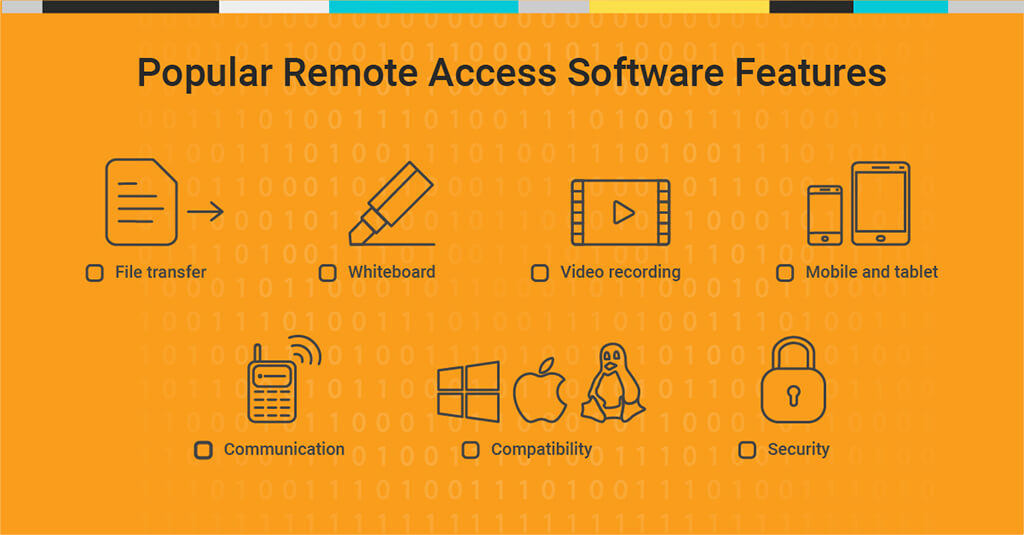
Generally speaking, some of the most common basic elements of remote access tools include:
- Drag-and-drop file transfer: With this feature, you can transfer files between machines without needing to use email or additional file-sharing programs. You can even print files off other devices.
- Desktop shortcut: If you need to access a certain PC consistently, it might make sense to have a desktop shortcut available.
- Whiteboard: This capability makes it possible to make visible marks on screen for added emphasis, which is useful for collaboration.
- Video recording: Recording your troubleshooting session or taking screenshots can be a valuable reference later.
- Mobile and tablet access: In some cases, you may be able to access a desktop with an Android or iOS smartphone or tablet for on-the-go troubleshooting.
- Communication: It can be easier to talk about a problem within the platform. Useful communication features include chat and VoIP.
- Compatibility: The most useful remote access software will be able to run on Windows, macOS, and Linux—and potentially additional platforms.
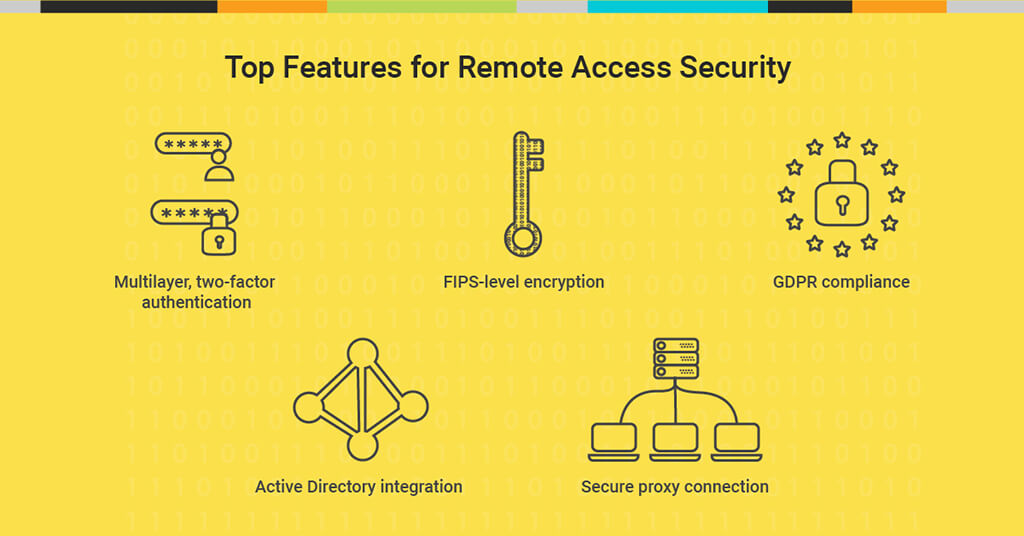
- Security: Remote access demands reliable security features and practices, including robust encryption, multifactor authentication, and Active Directory integration.
Using Remote Access Software for Businesses
The ability to remotely view and access computers can open up a range of possibilities for businesses. In the right context, simply sharing a screen view can be a powerful function unto itself. Generally, remote access software can be sorted into a couple types of major use cases that are relevant for businesses: individual or peer use and IT troubleshooting.
At the peer-to-peer level, employees can use simple remote access software for collaboration. Sharing a screen view can facilitate quick training or demonstrations, especially since whiteboard features allow users to draw lines to emphasize aspects of a presentation. Basic remote access software also enables file sharing (even across an employee’s own remote devices) and video conferencing for meetings. But while basic screen-sharing tools are often appropriate for these use cases, for reliable service, it’s best to go with an enterprise-grade option.
Remote device control is even more valuable for IT professionals, but it demands high-quality and secure software. This holds true for businesses of just about every size and type. Such solutions are popular with enterprises that have in-house IT teams, especially those with dozens or hundreds of employees, multiple offices, remote workers, or global operations. Remote capabilities are particularly critical for managed service providers working with SMBs—having an appropriate remote access tool is all but necessary for expanding their customer base. Making in-house service calls can be costly and time-consuming, but remote access makes it easy to troubleshoot from anywhere in real time.
It can make sense for an IT department to use remote access software to perform a range of routine management tasks across employee devices, including security updates, software downloads or updates, or settings changes. That said, remote access software is perhaps uniquely useful for troubleshooting. At many businesses, the sheer volume of troubleshooting tickets can quickly overwhelm IT staff if they have to perform them in-person. With remote software, however, IT can serve as a “help desk” and perform efficient, effective diagnostics and fixes as needed.
Because IT needs to do much more than share displays, remote tools for businesses typically offer more complex security features and more granular configurations. In fact, many of these tools are quite sophisticated, and provide built-in analytics features. There are a number of distinct advantages for businesses that choose to use remote access software for troubleshooting:
- Speed: When it comes to protecting a device or network, speed is of the essence. When IT can address individual problem computers immediately, it’s able to head off bigger security incidents. What’s more, the troubleshooting itself can be completed more quickly so that IT can move on to the next task without delay.
- Flexibility: Remote can also mean convenient. Using remote access software, IT can address problems from anywhere—sometimes even from mobile devices—without the hassle of physically traveling to the problem device.
- Scalability: Depending on licensing, remote access tools may be usable by multiple IT technicians and will likely allow for access to dozens or hundreds of end-user devices. If a business grows, IT capabilities can scale up right alongside it.
- Recordkeeping: Using remote access software makes it easy to create a “paper trail” of ticketing receipts, response summaries, screenshots, videos, and more.
How Does a Remote Troubleshooting Session Work?
A common remote access scenario might involve an employee in another city requesting help with an unknown issue that is affecting core computer performance. The employee might submit a ticket to the IT help desk along with any IP address or authentication information that’s needed.
When it’s time to address the ticket, a technician will log in to the server device remotely, being sure to follow any and all relevant security protocols. In some cases, the technician doesn’t need the end user to be present and can access even a crashed or sleeping computer; in others, the end user must be available to verify the remote access request. At this point, it may become necessary to communicate directly with the end user to learn more about the issue or provide guidance as to how they can address the issue themselves in the future.
If the issue isn’t immediately clear, the technician can take a look around to identify potential culprits. In this scenario, they would need to use a robust remote access tool that goes beyond simple screen-sharing and includes built-in troubleshooting features like historical and/or real-time analytics. The technician will check event logs to find performance issues, or may choose to view processes, stop processes, or run script to pinpoint the issue.
In the majority of cases, remote-control tools can give IT the access it needs to gain in-depth insights and troubleshoot effectively. Of course, remote access software can’t help with certain types of hardware problems, or if a device is disconnected from the internet. In these cases, an old-fashioned phone call might have to do.
Is Remote Access Software Secure?
It’s fair to ask whether remote access software is secure, as there have been some notable breaches of specific remote access products in recent years. For instance, Symantec’s pcAnywhere software was famously compromised in 2012, resulting in the company discontinuing the product. In 2016, a number of TeamViewer users reported signs of remote hacking, potentially stemming from users’ failure to adhere to login best practices. Because of the sensitive nature of remote access, these programs are tempting targets for hackers, especially if the user has an inadequate remote access setup with weak password protection.
Further, there are certain remote access use cases that may put business data at risk. For instance, a small company could conceivably use remote desktop software to access a server that contains a specific application or data. By doing so, the company would avoid duplicating data or needing to buy more than one application license. While this would certainly be convenient, it would also create potential vulnerabilities.
Unfortunately, hackers can use remote desktop software to access and steal sensitive data—or even deploy ransomware that holds the data hostage. How would this happen? If a business fails to implement security measures like multifactor authentication, hacking their systems could be as simple as “guessing” a password (which, with a password-hacking program, may take only a few hours). This is why it’s crucial to follow security best practices when using remote access software.

The best remote access software comes with robust security features included. Look for high-level encryption that follows Federal Information Processing Standards (FIPS). PCI-DSS regulations recommend features like Smart Card logon, and while these can be helpful, some form of multifactor authentication is crucial. In some cases, remote access software can even integrate with Active Directory so that you can centralize how you manage technician sign-ons.
Choosing a Remote Access Software Solution
There are a variety of remote access software solutions currently on the market. Many of them are well-known and are often appropriate for certain basic remote access scenarios. That said, it’s important to thoroughly vet your options if you intend to use them in a business environment, as not every tool can do everything.
As a rule of thumb, it’s best to steer clear of free options that usually don’t provide the functionality or security features businesses need. Instead, look for enterprise-grade solutions offering robust security and smooth functionality at a price that fits your company’s budget. Of course, no matter what solution you choose, be sure to enforce IT and employee best practices for utilizing the program.






